Project security is divided into 2 main parts – server security and application security
Server Security:
We use an internal security protocol to restrict access.
Access to the production server is provided only to two types of users – DevOps and CTO.
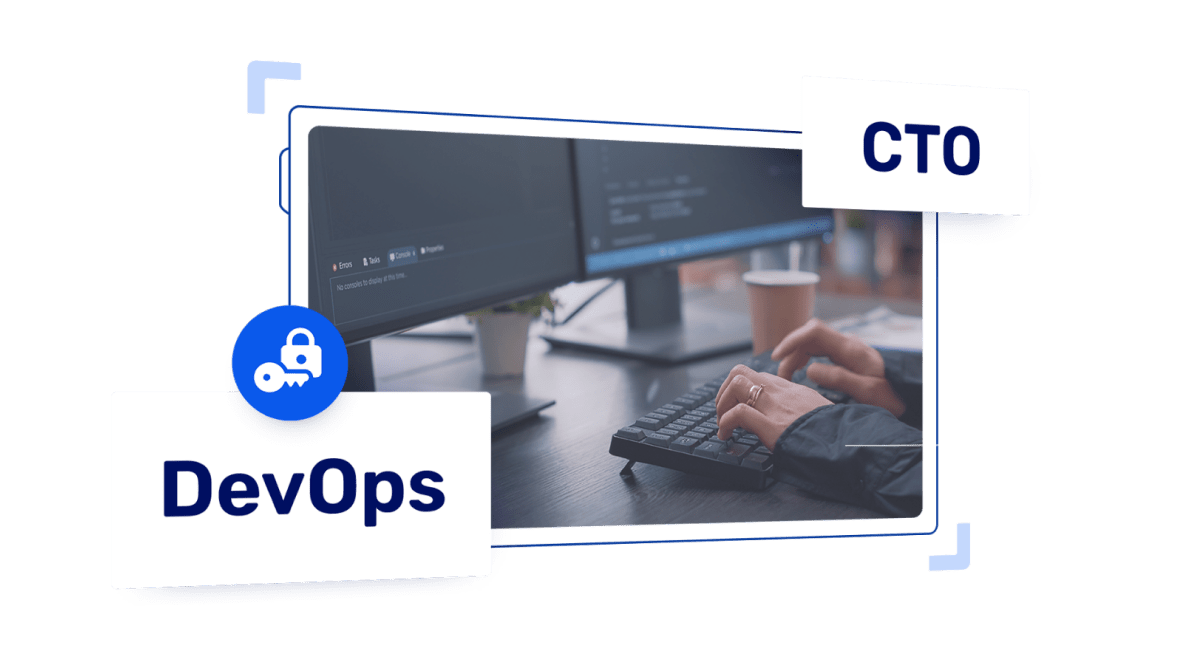
Malware/spyware:
On the production server, we have a firewall to prevent malware attacks.
Servers use the HTTPS protocol to protect user data.
Backup
Our backup system saves a server image every 3 days and keeps the information until the next backup.
The database and content can be restored at any stage, depending on the last point in time when the backup was made.
Video hosting
Video storage and streaming is handled by VIMEO, a recognized third-party system
with independent security.

Application Security
The system is divided into two independent parts. Frontend and Backend. Each part is on a separate server.
All development is done using the REST architecture. User passwords are not stored in an open format.
We are using a JWT token for authentication. The interface is written in the Angular design language.
Sanitization and XSS injections take place in this structure, which prevents internal failures of security components.

Leave a request and we will contact you in advance
Want to produce a digital course and enjoy close support the whole way? Leave details and we will get back to you soon!
